What is the Dark Web? And how can it Impact Your Business?
What is the Dark Web?
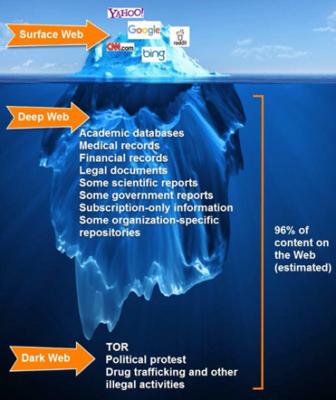
The internet is actually made up of three different layers: the surface web, the deep web and the dark web. The top layer, the surface web, are web pages that show up using search engines such as Google – like the Kinkayo website that you’re looking at right now.
Deep Web Vs. Dark Web
You may have heard of the dark web and deep web but do you really know the difference? Most people actually don’t – after you read this blog you’ll be one of the few <5%, who actually do.
THE DEEP WEB
So let’s start with familiar territory. Did you read your emails at work today? Have you checked Facebook Messenger? Or downloaded a PPT from your private Dropbox? If you did any of these, then you accessed the deep web.
The deep web isn’t some mythical place. Instead it is the collection of websites on the internet that are hidden and accessed via passwords and authentication. It is a parallel internet of sites that can’t be accessed through the world wide web. Any time you log into an account – any account, you’re accessing deep web content that won’t show up on a search engine. For example, work intranets, password-protected areas of online banking and draft blog posts (such as this one 🙂 are all stored on the deep web.
This means that if someone was to search for you on Google, your banking details or Tinder profile won’t show up in the results. The deep web is about 95% of all the data available online, which isn’t surprising when you think about the amount of private data there really is.
THE DARK WEB
At the bottom part of the deep web lies the dark web. The dark web is similar to the deep web in the respect that it is hidden from the normal web. However the dark web is not information that is not linked, but purposely hidden. To access the dark web you need to use special web browser, the most popular of which is TOR.
How does TOR preserve anonymity?
Basically, a network of volunteers’ computers bounces traffic around the globe, which prevents anyone conducting network surveillance or traffic analysis from being able to discern a user’s location or usage. Data gets encrypted at each bounce until it reaches its destination, where it is decrypted without the final destination being able to tell where it has come from. Though the deep web makes up 95% of all the internet the dark web only consist of about .03%. But that small section has millions of monthly users. Thedark web is usually what people actually mean when they refer to the deep web.
While it requires special software, tradecraft and resources, it’s just a matter of steps to set up that provide a way in for those looking to join the dark web and keep info such as their IP address hidden.
When people use the world wide web – the one we use every day and access through Google – everything is recorded somewhere. IP addresses can be tracked, and any site hosting illegal material will soon be shut down by authorities.
The Dark web, however, is a different place. Two thirds of the dark web is made up of the sale of drugs, guns and other illegal products – one third actually consists of something much more valuable – stolen corporate data. For companies, the most important data dumps include their leaked emails containing their intellectual property, pricing information, employee logins, ID documents for C-suite and up to the Board level.
How Someone Targeting Your Organization Gets your Data
Many companies assume that their data is safe. Often, the Managers at IT teams start and end with anti-virus software and firewall deployment. Security for their data is mistakenly seen as “a technology problem” – one that can be easily solved with updated anti-virus and firewalls. The threats, they believe, will come from external sources.
This common misconception gives the impression that more infrastructure and systems will stop these incidents. While this may sound productive – the reality is that there is only so much these solutions can do to stop attackers – especially hackers who are highly motivated, and very well-funded.
Instead of focusing solely on the immediate “crisis” of an incident responding to – managing and resolving a data breach – companies must have a way to detect the sale of their data on the dark web if they really care about their information security, GDPR, their staff and customers. They need to identify how their company data is being stolen and exploited, and then look to shore up and reduce their vulnerabilities.
Once a breach occurs, it is safe to assume that fraud will ensue. This could be immediately after or days, months or even years down the line – such as with the compromise of 3 billion Yahoo! email accounts that were discovered at the end of September 2016, but which Yahoo! believed actually started in 2013-2014.
Companies thus need to be aware of the data they consider valuable and determine how to keep that safe. By devoting equal energy to this portion of the data breach lifecycle, businesses can better address and protect consumers.
On this front, the good news is that there are 3 things Companies can do to reduce their exposure.
- Invest in services to Find Your Data in the Dark Web
If a company has been breached, it is likely that any information stolen will appear on the dark web before the attack has even been detected using conventional tools.
That’s why companies should focus on using tools that keep track of their data, as well as securing their networks. But now, there’s technology that allows you to continuously monitor for your data outside the firewall – which means that if you suffer a data breach that is openly discussed, shared or published, you’ll know about it within minutes and can proactively alert staff who have been affected.
- Proactively provide fraud detection to customers.
There is a clear consensus that identity protection products are the best defences for consumers following a breach, and these should become ongoing services rather than just a post-incident fix. By offering these protections proactively, businesses can accurately verify their staff and customers on an ongoing basis, rather than just reacting to the consequences of a breach.
- Strengthen internal security practices
While considered “good housekeeping”, many companies struggle to protect their own networks. In fact, KPMG and the Wall Street Journal reported recently that the majority of companies believe employees are weakest link in their efforts to create a strong security posture, with more than half experiencing a security incident or data breach due to employee negligence.
Most likely the result of inadequate training, there is a clear knowledge gap that businesses must address by educating their employees on data security and creating a culture of cybersecurity awareness. This includes making sure training involves emerging security risks and is mandatory for all employees, providing incentives to employees for proactively protecting sensitive information or reporting issues and having clear consequences for employees causing a breach.
Failing to devote time and resources to security awareness only creates more vulnerabilities as employees – through no fault of their own – are left to protect their company’s valuable data. This is true for all departments and levels of employees – from IT teams responsible for upgrading security patches and anti-virus software to HR departments responsible for safekeeping employee information.
Finally – it’s really important for businesses to invest in the right tools that can help them find their data, no matter where it’s hidden. Having the ability to monitor the millions ofdark web pages, paste bins, and underground forums and then being able to filter and extract that information based on things like customer databases and employee email addresses – is a necessity for businesses. While taking advantage of them requires businesses to be more hands on, it is well worth the effort when you factor in the reputational and financial risks of a data breach and the impact on your company.

